Just some personal notes and thoughts about a different approach to cybersecurity defense system.
In the cyberspace the scenario in which every day an Information System (IS) lives is more or less this one:
- It could have a cyberattack by bad guys/organizations;
- If the cyberattack has success the Information System could be compromised in a hide or manifest way;
- If we realize that the Information System is compromised, we start the security crisis management;
- After the incident management we analyze what happened and try to harden more the defense system.
Cybersecurity attacks
The cyberspace is not a secure world you can be the target of many types of attacks, for example we can have:
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks;
- Man-in-the-middle (MitM) attack;
- Drive-by attack;
- Password attack;
- SQL injection attack;
- Cross-site scripting (XSS) attack;
- Eavesdropping attack;
- Birthday attack;
- Malware attack;
- Phishing and spear phishing attacks;
- And so on.
Cybersecurity HIDE incident
If the attack has been success but we don’t have any idea about what’s going on. This is the worse situation in which we can be. No one alerts us about it. The question is: where is my high defense system? In this situation only a very smart and good monitor system can detect that my system is compromised and where is the problem.
Cybersecurity manifest incident
If the attack has been success and we realize that our information system is compromised we can only face and manage the incident, which could be:
- A Data leakage of any type: mails, photos, credit card data, sensitive personal data and so on;
- A Crashed web sites;
- A Breached networks;
- A Denials of service;
- A Hacked devices;
- A Organizations’ decrease of reputation by leakage of information or successful cyberattack with huge economic loss;
- A Personal loss of reputation;
- And so on
Post-incident analysis
In this phase it occurs to assess the causes and to analyze the company’s crisis management capabilities in order to eliminate deficiencies in the cyber defense system to improve its resilience.
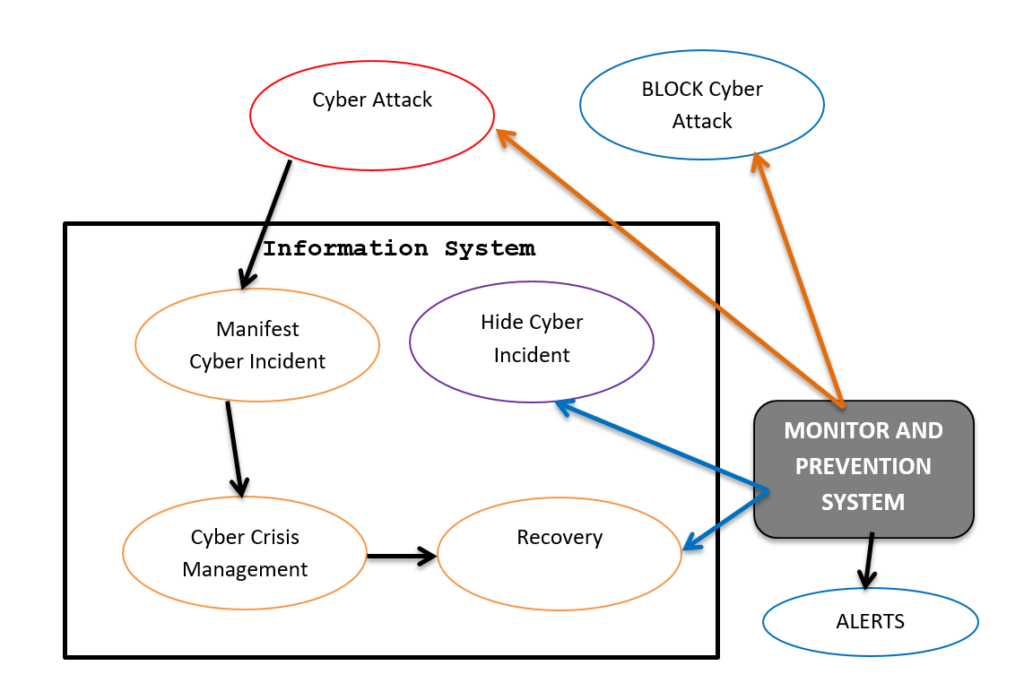
First Line of defense model
But what is the first line of defense model? As we can see in schema is the monitor system. It is very important and its role is crucial and fundamental. Every slice of second it has to tell us:
- First of all I’m good I’m working well, I’m not compromised;
- the IS is not under attack;
- the IS is working according the specifications and it is not compromised.
or:
- The IS is under attack but it is not compromised and I immediately inform the emergency team to stop it.
- The system is compromised I didn’t detect the intrusion but I realize that the attack had success we need to recovery. This is the worse situation but the monitor immediately alert system advises about it in order to contain the damage.
Or:
Anyone of the above sentence is a fake news. This means the monitoring system does work well. In this case we are in the very bad situation that we need to minimize by increasing and improving the capabilities and intelligence of control and auditing every days of monitor system.
But what does the monitor mean?
Monitor means to check, to verify that everything is working according the rules and specifications.
The monitoring activity should be at different levels:
- Network level that is packet analysis and so on;
- Operating system level;
- Application Level;
- User behavior;
and it should analyze, combine and correlate events at different levels for a better control of IS. I think we can have the last defense technology but without a very smart monitor working 24/7 on the information system we don’t have a good cyber security system.