Email attachments are one of the main vector of malicious code. According to analysis by Helsinki-based security provider F-Secure 85% of all malicious emails have a .DOC, .XLS, .PDF, .ZIP, or .7Z attached.
But now, in addition to them, we have to consider another type of dangerous attachment .HTML.
When we receive an email with an attachment of .HTML type, we have to be very careful and don’t’ open it. The .HTML file could contain, for example, these dangerous JavaScript code:
<body onpageshow="document.location.replace(window.atob('a base-64 encoded string'));">or
<frameset onpageshow="document.location.replace(window.atob('a base-64 encoded string'));">
It is used onpageshow event because it occurs every time the page is loaded, while the onload event occurs only when the page first loads and it does not occur when the page is loaded from the cache.
document.location.replace(newURL) replaces the current document with a new one.
The atob() method decodes a base-64 encoded string encoded by the btoa() method. The base-64 code string obfuscates the URL it represents.
In the second code snippet we can notice the use of <frameset> tag which is deprecated, no longer recommended and not supported in HTML5. Anyway some browsers might still support it for compatibility purposes.
The problem is that the JavaScript code inside the HTML page can load any URL page, and only decoding the “base-64 encoded string” you can know which web page. The decoding of base-64 string is done dynamically by atob function when the web page is showed in the web browser. So, if you open the file, it is already too late in case of malicious web page.
With malicious code in a web page we can have:
- Malicious Ads: they are advertisements on the Web that infect the user's machine with malware in order to make the compromised machine a member of a Botnet.
- A Malware Distribution Network (MDN): it is a collection of landing pages, malware repository servers, and standard redirection pages. The goal of an MDN is to redirect the victim from a landing page to a malware repository server.
- Drive by Downloads: it refers to the automatic download of software to a user's device, without the user's knowledge or consent.
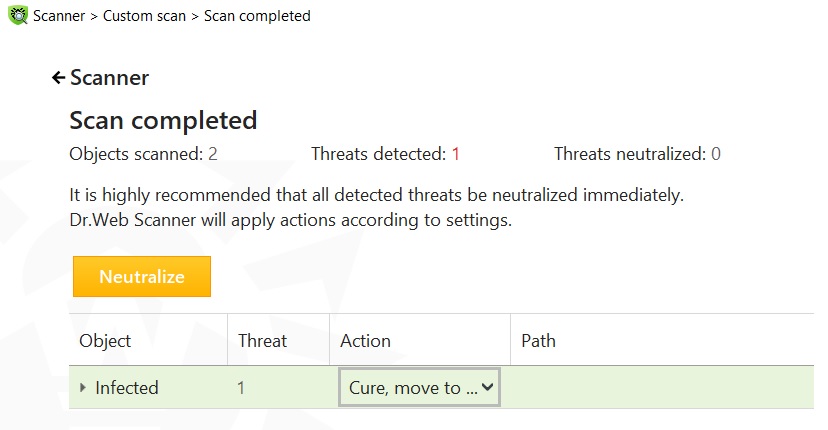
Here it is how an antivirus reacted when it scans this type of HTML attachment: